TWD Industries AG – Remote-Anything.com (1999-2009)
"What GOOGLE's chief executive, Eric Schmidt, has to fear more than anything else is that he'll awake one day to learn that the GOOGLE search engine suddenly doesn't work on any Windows computers: something happened overnight and what worked yesterday doesn't work today. It would have to be an act of deliberate sabotage on MICROSOFT's part and blatantly illegal, but that doesn't mean it couldn't happen. MICROSOFT would claim ignorance and innocence and take days, weeks or months to reverse the effect, during which time GOOGLE [initially named "BackRub"] would have lost billions."
–The New York Times, "Chrome vs. Bing vs. You and Me", July 12, 2009
That cannot happen: the shareholders of the U.S. $10T GAFAM use them as a weapon to destroy all competition.
MICROSOFT MS-DOS (1981) was a rip-off of DRI's C/PM (1974) wrote the U.S. dept. of Justice which awaited a decade – and the death of the stolen company and founder – to see unlawful misconduct despite having conclusive evidence since day one, to finally let MICROSOFT settle for 1% of the prejudice, the day before the trial. The result of rewarding crime is... more crime.
Designed, implemented and marketed by TWD Industries LLC founded in 1998 in the USA by a former Nasdaq:SPCO engineer, Remote-Anything (RA) was small (90 KB), portable, easier to use and to deploy, faster, much safer, more stable, had many more features (some still exclusive in this segment today) and was 3.7 times cheaper than SYMANTEC pcAnywhere (53% of the market).
After 6 months, RA was doing so well that the Antivirus products of SYMANTEC (87% of the market at the time) and KASPERSKY (initially getting most of its revenues from SYMANTEC) started to delete RA, claiming that it was an unfortunate (but constant) string of "accidental false-alerts".
After 5 years of this guerrilla, as governments, manufacturing and energy plants, and many other large users officially asked these anti-virus companies to stop deleting their licensed RA copies, Eugene KASPERSKY changed the narrative and wrote me that "RA qualifies as a backdoor-trojan because it can be installed silently".
RA, as a single 90 KB executable file without dependencies, merely required end-users to copy it on a machine to then run it with a simple mouse-click. A dialog-based installation procedure would have been pointless to copy and run one single file: in contrast with pcAnywhere's myriads of files and hundreds of MBs stored on installation CD-ROMs, there was nothing to "install" with RA.
But SYMANTEC pcAnywhere had the "litigious" silent-install feature documented in "Symantec pcAnywhere Administrator's Guide": "Configure the installation to run in interactive, passive, or silent mode" so, under his own "backdoor-trojan" criteria, Eugene KASPERSKY should have qualified and deleted pcAnywhere like RA. Of course, he never did it – that would have been the end of his business.
Why stick to reality when your sponsors can have all tribunals deny it, right?
The pcAnywhere silent-install feature is still documented by eWeek.com:
"The InfoSec analysis also claimed Symantec had developed an installer that installs newer versions of pcAnywhere in silent mode. It could be possible to use the code to make a modified version of pcAnywhere which users could be tricked into downloading. Once downloaded, it would act as a back-door application for researchers to use to compromise the system".
Further, MICROSOFT Systems Management Server (SMS), like the recurringly-hacked MICROSOFT Windows Updates, allowed to deploy software on a network and do silent unattended installations, a "common and legitimate feature" ...completely bypassing end-user consent (as opposed to RA which required to be copied and clicked by end-users). So, invoking it as a pretext to delete RA (which did not implement any kind of installation process – silent or not) was just a fallacy:
In 2003, the Renater Community Emergency Response Team (CERT) published an electronically-signed document stating that "VNC [AT&T], pcAnywhere [SYMANTEC] and Remote-Anything [TWD Industries] are commonly used as backdoors".
Yet, SYMANTEC, KASPERSKY, MICROSOFT and the MICROSOFT VIA (Virus Information Alliance) have never used their antivirus products to delete pcAnywhere, demonstrating their double-standards, and, given their chosen judge and party posture, their illegal anti-competitive practices.
TWD has responded with the Directory Server (DS), which allowed people to securely deploy (with a simple mouse click) RA (or any other software) on a corporate WAN (Wide Area Network) without having to configure any PC, LAN IP address, firewall or router, and adding to RA WAN-management features found only in eye-wateringly expensive (and horribly complex to deploy) suites like "Intel LAN Manager" and "MICROSOFT Systems Management Server".
By eliminating the costs and delays of large-scale deployments, RA became uniquely useful to very important Windows users. More than 280 millions of Remote-Anything (RA) licenses have been deployed in 138 countries.
To measure the extent of such a feat in the 1999-2004 years, this was done despite the constant anti-virus guerrilla and denigration campaigns: to poison search-engine results, even after TWD stopped to market RA, KASPERSKY alone was publishing year after year tens of thousands of new RA pages on its virus-list website (several orders of magnitude more than TWD ever had published releases).
Destroying TWD's reputation via internationally-coordinated defamatory publications failed. Many end-users, large and small, have uninstalled their anti-virus – not to protest, but merely to keep using RA which was vital to their activity. Merit and honesty prevailed... because many people were still, at this time, spending their own money earned via common-sense and hard-work.
Then MICROSOFT "Windows Defender" and the whole MICROSOFT VIA (Virus Information Alliance) started to delete RA, stating that... "RA is not a virus" [1, 2].
TWD sued for anti-competitive practices five US companies selling 'Enterprise Network Management' products competing with the RA/DS they were sabotaging (by corrupting their options stored in the "Windows Registry") and by deleting the RA executable file.
The Department of "Justice" fined TWD, flatly ignoring all the officially-collected evidence and deciding that it was legitimate for these companies to automatically and silently eradicate a competing U.S. product relying on a patented technology making RA naturally immune to network scanning and attacks
[3,
4,
5] – a desirable feature for end-users, but apparently not for the MICROSOFT Windows security ecosystem.
Late 2008, after most users had migrated to the most recent version of Windows, it was no longer possible to sell the RA and DS products automatically and silently deleted by MICROSOFT "Windows Defender"... in the total indifference of the judicial authorities (MICROSOFT and its VIA falsely claimed that end-users had the possibility to spare RA by creating "an exception" – but this feature, strangely, was not working for RA).
Irony of fate, in 2016, more than a decade later, Eugene complained about Microsoft "Defender", unable to resist the temptation for tasty snacks, playing dirty tricks against its own "strategic partners":
"When you upgrade to Windows 10, Microsoft automatically and without any warning deactivates all 'incompatible' security software and in its place installs... you guessed it – its own Defender antivirus.
Even if users have compatible protection from an independent developer already installed, Defender appears with an alarming window. It fairly shouts that Defender is switched off, because you've some other AV installed. There's a big juicy Defender 'Turn on' button too. Of course, many users will be inclined to press this button: 'well, it's from Microsoft – the people who make the OS; must be good; no harm in turning it on for sure'.
Microsoft is gradually squeezing independent developers out of the Windows ecosystem if it has its own application for this or that purpose.
In doing so, Microsoft is acting against the interests of users since a lot of its products are of inferior quality. Browsers, gaming hubs, image viewing, processing of multimedia files and PDF documents, cybersecurity and many others are already suffering from this and, as a consequence, so are users." –Eugene Kaspersky
Eugene, there's only one way to show the World that you are not like them – show that you have learned your lesson, and behave better:
"Errare humanum est, perseverare diabolicum".
Rest in Peace Remote-Anything (1999-2009).
Not really. Wrongdoers need to rewrite History to falsely represent themselves as "the white knights saving the World" and their victims as "the bad guys" deserving their sad feat (prematurely contributing with their dead body to fertilize the ground they have defended against the Robber Barons "legitimate owners of everything"). Something is theirs once they took it by force and/or with lies, but the politesse cannot be returned – that would be an outrage made to their "superior moral status":
SECRET//SI//REL TO USA/, FVEY
DISRUPTION
Operational Playbook
- Infiltration Operation
- Ruse Operation
- Set Piece Operation
- False Flag Operation
- False Rescue Operation
- Disruption Operation
- Sting Operation
SECRET//SI//REL TO USA/, FVEY
That's what they call "the free and open markets".
So, more F.U.D. (Fear, Uncertainty and Doubt) was required to further tarnish the name of RA – even after it was illegally eradicated from the market – with the assistance (again) of complacent government authorities:
"MITRE was established to advance national security in new ways and serve the public interest as an independent adviser. Our non-profit status sets us apart. Motivated by impact, our people discover new possibilities, create unexpected opportunities, and lead as pioneers for the public good."
For the [1999-2012] period of time, Mitre.org lists:
• pcAnywere: 18 vulnerabilities (including remote arbitrary code execution)
• Remote-Anything: 1 vulnerability (1) found in 2012, 4 years after TWD stopped to market RA in January 2009, (2) falsely represented as empowering "remote attackers": the incriminated RA Player (aimed at playing recorded RA sessions) was NOT a network program, and (3) requiring to play locally a manually-crafted file (due to RA session authentication and encryption, this "vulnerability" was not exploitable in a live RA session, and no recorded RA session could be saved as a file to trigger it).
This single vulnerability was due to a 50-year old defect of all U.S. operating systems left unaddressed by the GAFAM and the cyber-security industry but fixed by TWD... a fix immediately censored by MICROSOFT, the U.S. search engines, and a U.S. Defense "top-of-the-line" cyber-security contractor.
Lies, lies and lies. That's a good summary of what a cartel of well-funded companies (dictating their conduct to many governments) has used to eradicate... yet another small company which only sin was to deliver much better and cheaper products – without any funding, lobbying, and assistance of governments to sabotage the competition.
– Why some among us feel the urge to constantly cheat?
– They believe that they can't win if they can't choose (1) their competitors, (2) the judges, and (3) the rules of the game.
"Tricks and treachery are the practice of fools, that don't have brains enough to be honest."
–Benjamin Franklin (1706-1790), one of the Founding Fathers of the United States of America
Cheating be can be sanctioned (and therefore discouraged) when its perpetrators are a powerless minority – but dishonesty becomes a major problem if our society is run by criminals (the 1%) because then their victims (the 99%) will have no possible recourse. Inevitably, ever-growing abuses will cause an existential threat to society:
"A lack of beneficence will make a society uncomfortable, but the prevalence of injustice will utterly destroy it."
–
Adam Smith, Scottish economist (1723-1790)
Eventually, at a given level of this manufactured chaos, the people will organize and react to merely survive – and the criminals will have nowhere to hide. When will they learn?
"Those who cannot remember the past are condemned to repeat it."
–George Santayana (1863-1952), "Life of Reason, Reason in Common Sense" (1905)
In 2009, TWD published G-WAN, a Web Windows Application Server that was several orders of magnitude faster in user-mode than IIS in the Windows kernel – on the top of supporting 18 scripted programming languages... and which still enjoys a zero-vulnerability status since its publication (yet another exclusivity in the server market).
To discuss the acquisition of a G-WAN source code license, MICROSOFT organized a conference call with 5 top-level executive directors. Having just spent $7.5Bn to upgrade IIS v5 to v7, the director of the IIS division killed the deal (in a reflex of self-preservation):
IIS 7 was 4 times slower than G-WAN for tiny 100-byte static files, and tens of thousands of times slower than G-WAN for large dynamically-generated contents... making it obvious that these $7.5Bn were not given to the lucky ones for their technical excellence.
That's what the Pharaonic Capitalizations and Mergers & Acquisitions celebrated by the media are for: siphoning pension-funds (public taxpayer money) – spoliation at its best.
These frauds hit end-users (forced to spend more than necessary) and shareholders (funds are stolen by publicly-traded company directors).
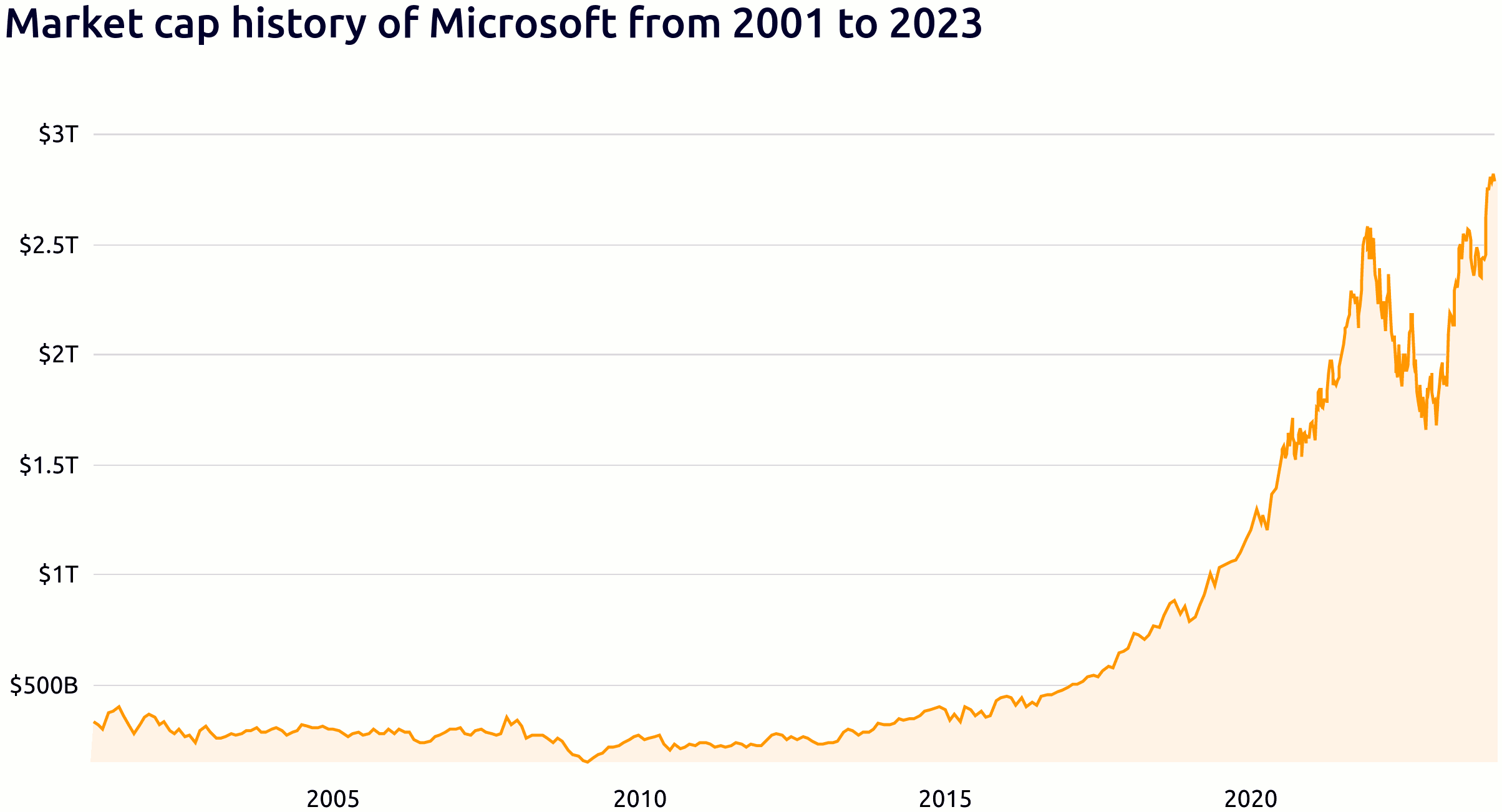
On December 23rd, 2023 MICROSOFT was 2nd in Market-Cap ($2.783 Trillion, a factor 100 gain each year for the 10 past years) – totally out of proportions with the economic reality: 23rd in Revenue and... 3,837th in Dividends (a very, very poor return on investment – that is, if you don't sell your shares to complacent central banks and pension-funds managing... public money).
Without any relation to their productivity growth (or decline!), the GAFAM quickly became the best capitalized companies ever seen in the history of Capitalism... to boost the outright fraud of private money-creation out of thin air and publicly-traded private companies – by several orders of magnitude.
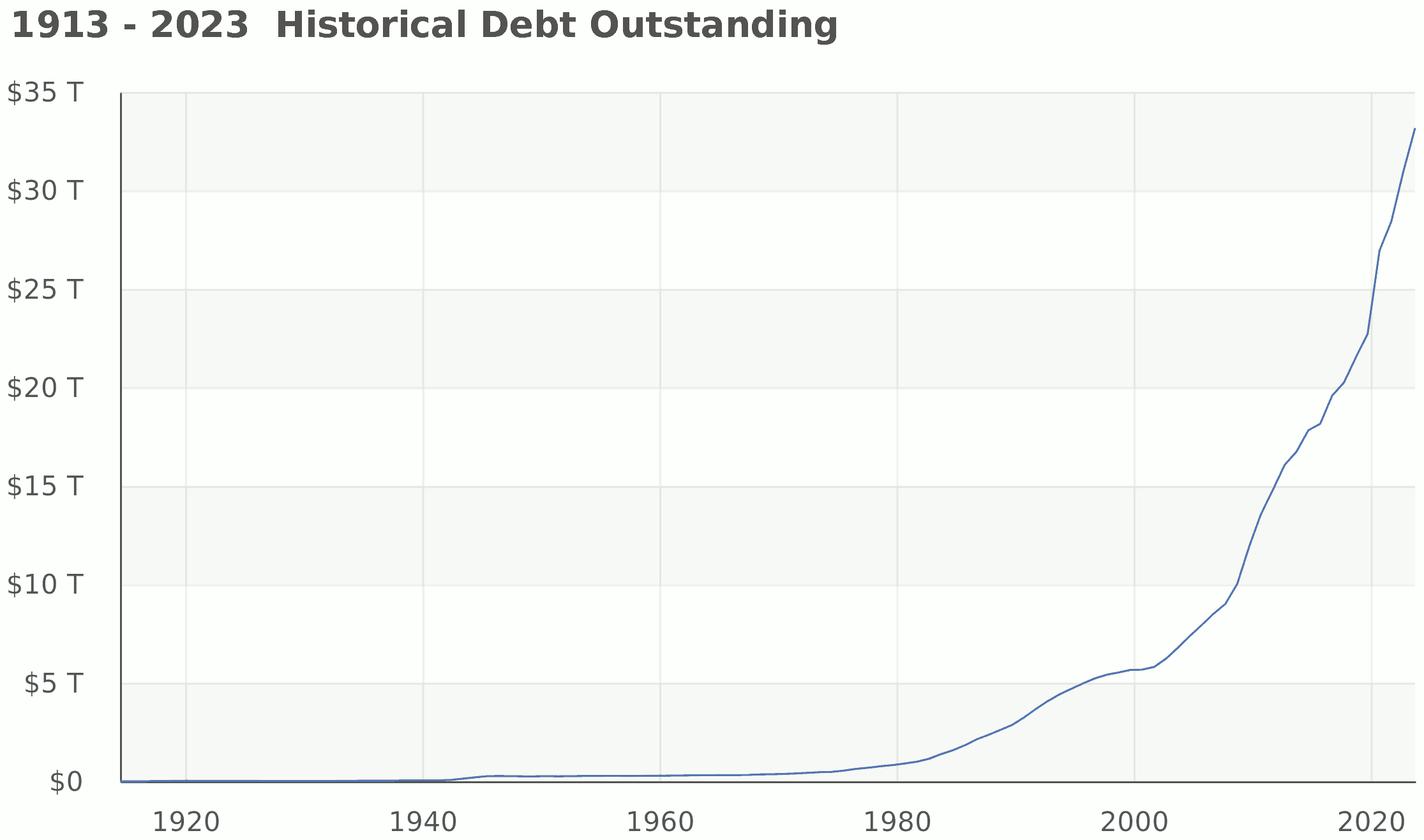
How do you think they all became so rich and arrogant? Simple: by taking the money from the pocket of the hard-working masses via public institutions (the poor cannot escape mandatory-under-the-law insurances, pensions and taxation), money which is then given-back to the very few tax-exempt rich via ever-growing public debt-funded public contracts, public investments, public subsidies, and... public fiscal and judicial leniency.
Our public administration is a gigantic racket and money-laundering machine, using the hijacked "rule of law" to steal the masses and enrich a very few protected by the varnish of respectability of a public system... created to enforce criminal policies... exposed as such 30 years ago.
Rather than making decent products, the pursued goal of this hyper-financed ever-failing industry is elsewhere: in outright mass-robbery. And, making this business-model sustainable requires to destroy all intellectual, economic and technological competition.
The same week, G-WAN was deleted by Trend Micro (a founding member of the MICROSOFT VIA)... without even trying to justify it – why bother, right?
So G-WAN was ported to Linux, a free operating system (funded by INTEL, IBM, GOOGLE, etc.) which does not need antivirus software and proved to be much faster and more scalable than MICROSOFT Windows.
This was the end of any chance to market G-WAN (Linux is an open-source platform and most of its end-users, small and large, are used to rely on gratis products, whatever their quality) but at least TWD's technical capacity had found an environment where it could survive.
Had they stopped there, History would have qualified these events are merely anecdotal. But if the illegally-inflicted damage is systematic, covered by the "Justice" department of all the vassal countries, and never-ever acknowledged and even less repaired, then this is obviously a tactic (striving thanks to the constant and total impunity of a very few acting like criminals at the expense of everyone else).
G-WAN was initially designed for Global-WAN (2010), a distributed Level-2 VPN based on government-audited (2008) "post-quantum" security (expected to be resistant to quantum-computers) or "unconditional" security (in academic jargon, mathematically-proven as "unbreakable") audited in 2008 and 2018 by two governments.
At least five governments have launched clandestine operations to sabotage licensing deals (the first one for $900 millions, and the most recent for $1+ billion).
That would have been legal if the same taxpayer-funded saboteurs had licensed the technology themselves instead of blocking every possible ways to market it, both for civilian and military uses... instead of exercising a passion for ever-failing much more expensive "solutions" that must be replaced periodically.
If the goal of this financial cartel is to eventually rule the World by ruining the taxpayer to destroy the concept of Nation, such a move makes perfect sense. But, under the rule of law, the civil servants (supposedly protecting the country and the taxpayer) that help these criminals are guilty of forfeiture.
After having addressed serious performance, encryption and secure networking, what remained to be fixed in our common infrastructure was "The Mother of All Backdoors":
In 2020, TWD shipped SLIMalloc, the first (and so far only one) memory allocator making the 50-year old C and 36-year old C++ programming languages "memory safe" by detecting, blocking and documenting in real-time "70% to 90% of the root causes of all vulnerabilities" that APPLE, MICROSOFT and GOOGLE keep reporting as "unfixable" [1] [2] [3].
As the simplest, most stable and efficient option available since Unix (C was created to write Unix), C is the programming language used to make all operating systems (MICROSOFT Windows, APPLE OSX and IOS, GOOGLE Linux and WebOS) – anything aimed to perform and scale (minimizing costs) – from the IoT to datacenters, and... unsurprisingly, all other programming languages (that also necessarily invoke system calls).
So, making C/C++ "memory-safe" (without slowing-down programs) is probably the most important contribution ever made to computer-science in the past 30 years.
In July 2022, after TWD weekly LinkedIn posts were showing to 18,000+ connections (mostly C-Level executives) how SLIMalloc was blocking zero-days documented weekly by TheHackerNews.com, the LinkedIn "professional network" owned by MICROSOFT has "suspended" the accounts of TWD's staff (making their profiles, comments, and posts invisible).
The same day all the related contents disappeared from all search engines and Wikipedia (where the CTO of a U.S. DoD and GAFAM Cyber-Security contractor, former DARPA project manager) later eradicated it repeatedly under the cover of several fake accounts.
The mere coordination of these actions is revealing of the nature of the
involved powers... and nefarious interests. Only constant illegal discrimination allows them to win – not only against TWD, but also against the rest of the world. And our governments are their toy: either enforcing these criminal policies or casting a blind eye to these recurring violations of the "rule of law".
Despite their ever-growing gargantuan financing and recurring golden public contracts, they:
• can only win by sneakily (1) spreading F.U.D. (Fear, Uncertainty and Doubt), (2) disqualifying the competition (with false-claims, arbitrarily-complex norms, with high-capital requirements, eye-wateringly expensive regulatory constraints, buyer-centrals imposed to large buyers), and (2) corrupt the ecosystem (distributors, financial intermediaries, large public and private buyers, etc.), the media and the judges so that the victims (end-users and competitors) have no alternative and no recourse.
• break the rule of law with total impunity, (1) allowed to use all illegal means to pursue the total destruction of all competition, while their competitors are (2) sanctioned for any remotely defensive action – like daring to ask tribunals to respect the law, or (3) speaking out when, finally, this remains the only available option.
• lose in the first place because (1) they constantly make sub-standard products (2) have a passion for planned-obsolescence to break things and force pointless new purchases of ever-regressing capabilities (if replacing C by MICROSOFT-sponsored C++ was "an insult to the human brain" for ACM-award Niklaus Wirth, guess what qualifier MICROSOFT C# deserves), and (3) they despise end-user needs:
"Since when has the world of computer software design been about what people want? This is a simple question of evolution. The day is quickly coming when every knee will bow down to a silicon fist, and you will all beg your binary gods for mercy."
–Bill Gates, MICROSOFT (initially named "Traf-O-Data") Founder,
Philanthropist
Philanthropist:
"one who loves mankind, or wishes well
to his fellow-men and endeavors to benefit them by active
works of benevolence or beneficence."
– The Century Dictionary
In the Financial Times' annual "How to Give It" issue,
Melinda French Gates highlights the catalytic power
of donor collaboratives to "address root causes
by changing systems".
No wonder about why they cannot afford to let any real competition exist: the "Robber Barons and Silicon Sultans" celebrated by The Economist would disappear overnight – and nobody among the unsatisfied 99% would miss them.
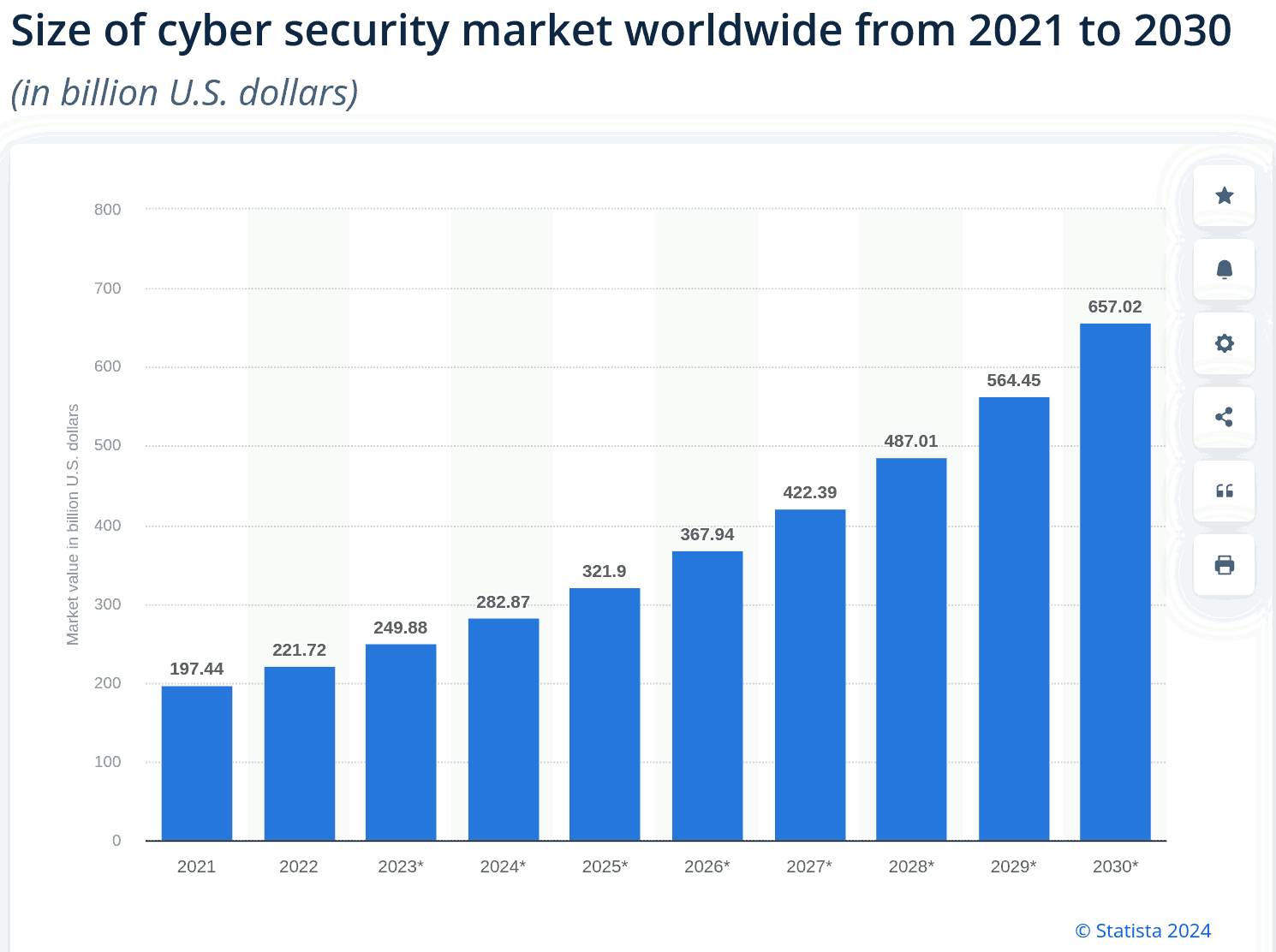
With SLIMalloc threatening "70% to 90% of the root causes of all vulnerabilities", the "private/public partnerships" (PPPs) collusion became even more apparent than in the chronic complacency of the dept. of "Justice". These golden public contracts are based on yet another USD 250bn a year scam (planned to tripple within 6 years – at the expenses of the taxpayer):
"We're talking to the big Internet majors, asking them to let us in via security loopholes, some accept, others don't. We probably need a law to compel foreign services, and it's coming."
–Gerald Moussa Darmanin, Interior Minister, April 28, 2021 (France Inter)
"For [the] encrypted messengers, such as Telegram, WhatsApp or Signal, [...] they go through Internet connections [...which] will allow access to the computer terminal of the person using these messengers [in order to access the plaintext, before encryption]."
–Gerald Moussa Darmanin, French Interior Minister, May 17, 2021 (assemblee-nationale.fr)
https://www.assemblee-nationale.fr/dyn/15/comptes-rendus/cion_lois/l15cion_lois2021093_compte-rendu
https://www.assemblee-nationale.fr/dyn/15/comptes-rendus/cion_lois/l15cion_lois2021093_compte-rendu.pdf
"How do you protect what you want to exploit?"
–Scott Charney, VP "Trustworthy Computing", MICROSOFT
Is the French taxpayer really willing to let non-elected politicians spend public money to surreptitiously penetrate his computers/tablets/smartphones/TVs/connected-cars at home or at work? Wouldn't public money be better spent at common-good expenses (like buying local and, at the same time, closing the backdoors once for all – instead of ever-funding the foreign backdoor-makers)? Why isn't it any public debate taking place about this ever-growing spoliation?
In November 2022, in the USA, the NSA publicly documented on its website:
"Malicious cyber actors can exploit poor memory management issues to access sensitive information, promulgate unauthorized code execution, and cause other negative impacts."
"Memory management issues have been exploited for decades and are still entirely too common today," said Neal Ziring, Cybersecurity Technical Director. "We have to consistently use memory safe languages and other protections when developing software to eliminate these weaknesses from malicious cyber actors."
"MICROSOFT and GOOGLE have each stated that software memory safety issues are behind around 70 percent of their vulnerabilities. Poor memory management can lead to technical issues as well, such as incorrect program results, degradation of the program's performance over time, and program crashes."
"NSA recommends that organizations use memory safe languages when possible and bolster protection through code-hardening defenses such as compiler options, tool options, and operating system configurations."
So, SLIMalloc, turning C into a memory-safe language, is a major achievement in computer-science and cyber-security (read our paper).
But, according to ALL our government officials, this achievement should never-ever surface because... public/private crookery – claiming to spend taxpayer money at securing the critical infrastructure while they do the opposite – must be protected at all costs:
"Across the federal government, about 90% of all spending on Cyber programs is dedicated to offensive efforts, including penetrating the computer systems of adversaries, listening to communications and developing the means to disable or degrade infrastructure."
–Rick Ledgett, NSA Deputy Director
We, the people, are the "adversary" claims Obama in his 2023 movie "Leave The World Behind" (Barack was executive producer and adviser on the script):
"With the right acts of digital sabotage, attack aircraft will be grounded, infrastructure disrupted and communications severed, reducing the enemy to a state of raging, pre-modern impotence."
–The Economist (2014)
This is why our infrastructure, IoT, mobile devices and computer CPUs have 5G kill-switches [1] [2] [3] supposedly protected by ever-failing (yet legally-enforced) "security standards" that must be changed periodically (instead of the 1948 safe-forever "unconditional security" that they openly admit is really, really not wanted):
"The move away from prescriptive standards towards a focus on outcomes under the NIS Regulations was welcomed because: standards are soon rendered out-of-date by fast-changing threats and the frequent discovery of previously unknown vulnerabilities".
–Cyber Security of the UK's Critical National Infrastructure (2018)
Beyond the obvious detrimental consequences for all end-users and the critical infrastructure (hacked, spied, sabotaged, ransomed – courtesy of an industry paid by the taxpayer without his consent(!) to generate vulnerabilities), that's a canonical illustration of the so-called "Free and Open Markets" and their legendary ability to self-regulate themselves for the sake of the now legendary "common-good":
"There's a market failure in cyber-security, made worse by the trouble firms have in getting reliable information about the threats they face."
– The Economist, "Market failures - Not my problem" (July 2014)
Can it seriously be called "democracy" when governments use their monopole of violence, taxation and infinite borrowing to private banks to protect and fund long-term criminal corporations (and reward their private shareholders with the compound-interests of the resulting fraudulent public debt) while denying all others access to the markets and the protection of the law?
Of course no. And 300 years ago everybody knew that the only way to avoid this trap is to randomly pick our representatives (99% of the population is not rich) rather than to elect the ones... chosen and sponsored by the rich creating money out of thin air.
Elections are the opposite of democracy because this kind of rich will always select and fund the candidates of their choice – for all the mainstream parties, just to be sure of never losing their grip on governments – here to "govern minds" (and to command on public money, "Justice", Police and the Army).
Bankers (BigCorp shareholders) love wars – hence the $5 trillion of taxpayer money given by U.S. politicians to the military-industrial complex since 2000. Bankers love healthcare – hence the $4.5 trillion of taxpayer money given by U.S. politicians to Big-Pharma in 2022 alone.
"When a government is dependent on the bankers for money, it is the bankers, not the government leaders, who control the situation, since the hand that gives is above the hand that receives. [...] Money has no homeland; financiers have no patriotism and no decency; their sole objective is gain."
–Napoleon Bonaparte (1769-1821), French emperor and military commander
"We know now that Government by organized money is just as dangerous as Government by organized mob."
–Franklin D. Roosevelt (1882-1945), 32nd U.S. President
"They who control the credit of the nation direct the policy of Governments and hold in the hollow of their hands the destiny of the people."
–Reginald McKenna (1863-1943), British Chancellor of the Exchequer, Chairman of the Midland Bank
This was so widely known that, during the 1789 French Revolution, the transition regime was officially called "The Regime of the Terror" (random civilian killings by armed troops) to make sure that the population would not interfere with the ones paid by the Calvinist Protestant English and Swiss bankers (the proxies generously rewarded for their crimes) to... enforce "representative democracy" (an oxymoron) via elections (like it was previously done by The Crown in the British Kingdom, and later, in 1776 North America).
It is important to make the distinction between the German Martin Luther Protestantism and the later kind that was managed by John Calvin (pretending to be French, despite an English firstname):
"They hold us Christians captive in our own country. They let us work in the sweat of our brow to earn money and property while they sit behind the stove, idle away the time, pass gas, and roast pears. They stuff themselves, guzzle, and live in luxury and ease from our hard-earned goods. With their accursed usury they hold us and our property captive. Moreover, they mock and deride us because we work and let them play the role of lazy squires at our expense and in our land. Thus they are our masters and we are their servants, with our property, our sweat, and our labor.".
–Martin Luther (1483-1546), "On the Jews and Their Lies" (1543)
It all started with the 1649 execution of king Charles I, at the initiative of Oliver Cromwell who, financed by a lender creating money out of thin air, took the seat he made vacant. As a "Christian Calvinist Protestant" (an oxymoron: the Christ rejected the cult of Mammon which in Hebrew means 'money'), Cromwell used his new powers to enslave and kill as many of the Kingdom's Catholics he could find, and swiftly organized the return of his ferociously anti-Christian sponsors to England... 365 years after their banishment by king Edward I in 1285.
"I am afraid the ordinary citizen will not like to be told that the banks can and do create and destroy money. The amount of money in existence varies only with the action of the banks in increasing or decreasing deposits and bank purchases. Every loan, overdraft or bank purchase creates a deposit, and every repayment of a loan, overdraft or bank sale destroys a deposit."
–Reginald McKenna (1863-1943), British Chancellor of the Exchequer, Chairman of the Midland Bank
Then, the British Kingdom's 1689 "Glorious Revolution" (the official name chosen by the assassins) created "representative democracy"... relying on carefully-selected London-residing politicians – the kind more concerned about their London bank account than about the ever-increasing problems of their remote fellows (Wales, Ireland, and Scotland).
The Bank of England, the model on which most modern central banks have been based after that, was established in 1694. The creation of the Press-Agencies followed-up quickly to control the narrative: the same foreign finance that was previously expelled for 3 centuries took the control of the British Kingdom in less than 45 years, by murder and corruption (to stay in power, a better story was needed).
In 1913, after the privately-held U.S. Federal Reserve Bank (FED) was finally established (several past attempts have failed, but the refractory Presidents quickly fertilized), the income tax (previously only raised in times of war) became permanent (to pay-back the interests of the since then ever-growing public debt): Congress added the 16th Amendment to the Constitution and the Revenue Act under which, individuals with income exceeding $3,000 were taxed at 1% and up to 7% for incomes exceeding $500,000.
Today, the rates are much higher, and the Sales tax (VAT in Europe) alone, paid at the same rate by the rich and the poor, is also much higher. Look no further to find how funding the private GAFAM was made possible with public money.
So, when we are told today that we have such flawed political and economic systems because we, the people, were stupid, uneducated or just not paying attention, this is a lie – made by a "controlled opposition" invited by the (subsided) media and generously paid to give conferences to spread disinformation... instead of being illegally censored and deprived from a living revenue – like those reminding you how this was done: by murder and extortion.
Terrorism
Terrorism:
"Policy of terror practiced during the French Revolution.
Exceptional measures to maintain a government, seize
power, achieve a political goal".
– CNRS
is officially defined by the French National Center for Scientific Research (CNRS)
as a government policy.
In 2015, Wikipedia suddenly felt the need to document the 1859 Carrington Event – and Hollywood relayed by Finance and the World Economic Forum (WEF) altogether state in January 2024 that:
"An orchestrated physical attack, electromagnetic pulse (EMP), cyber-attack, or geomagnetic disturbance (GMD) could shut down our electric grid for a year; or longer."
NOTE: a Natural event, by definition, cannot be "orchestrated". Yet, such an hypothetic event comes first.
"Extreme weather (66%) as the top risk faced in 2024, a Cyberattack with COVID-like characteristics (39%)."
NOTE: Cyber/EMP/Climate man-made events can falsely be represented as Natural events – while, by coincidence certainly, the wide public is deprived from the effective solutions [1][2].
"Everything that we rely upon would be gone. Within a year, 90% of the world's population would be dead from starvation, disease, or killing themselves in total and utter social catastrophe."
NOTE: This would explain why this century-old solution, presented by TWD at the Munich Security Conference 2019, has been – and still is – dismissed, despite (or because?) of its immediate benefits for the rapidly declining global economy and human development opportunities.
How has mankind reached such a sorry state of things?
- hunter-gatherers (scarce people, large territory, no "property" concept, total freedom, peace enforced as no family or small tribe has more power than others, courage, skills and generosity – the ability to share and be generous with those in need – are praised)
- small-scale sedentary agriculture (clever hard-working people have noticed that some places are better than others, and that grain/livestock can be selected and grown-up, reducing the uncertainties of bad weather, accidents, sickness, courageous preys, and in general poor food availability)
- parasitic nomadic armed robbers (barbarians devastating small peaceful defenseless communities that have invested their own time to grow their skills at managing land to grow grain reserves and livestock)
- small local governments impose their monopole on violence to defend "their" private property (armed robbers seize a territory, impose property laws, subordination and privileges, taxes in grain/livestock/tools to a defenseless working class)
- metal money (used by war kings to arm and pay foreign poor, ferocious mercenaries to let them conquer the World and extract more power: land, metal, spice, slaves, soldiers – to survive the ambition of other kings)
- parasitic paper money (used by fraud kings also called the international bankers, to first fund then later defeat the war kings by hijacking the "rule of law" at their sole advantage: legalized lies with legalized violence – an oxymoron since the "rule of law" imposes by nature a balanced agreement between all the involved fairly-informed parties)
- parasitic electronic money (an evolution of paper money which cost is even less and which amount can be augmented, reduced or confiscated by the press of a button – granting fraudulent sustainable totalitarian powers).
Human beings live by killing and eating other (vegetal, animal) organisms generated by mother Nature:
- Civilization is the consequence of the accumulation of goods (having more than needed has allowed to be safer ourselves, share more with those in need, and build more for all – within the limits imposed by Nature) – it should result in more freedom rather than slavery.
- Money (necessarily imposed by murder to convince the free to become a slave under a treacherous "rule of law") has allowed even more accumulation, hence its success (without any more limits when paper/electronic money has replaced precious-metal coins, scarce by-definition).
A financiered economy (based on creating money out of thin air), a twisted invention aimed at robbing the kings and the workers, is the only thing in existence requiring an infinite growth to stay afloat because debt can only be paid-back with more debt (it is therefore well-known as eventually doomed to fail – and does so periodically).

In this model, the people have to please their masters and to work hard in the hope of being allowed to make money as slaves of those making money by the press of a button to trade fiat money (fiat means 'trust' in Latin) into tangible goods.
And, if you think you are not a slave yet, ask yourself who is building the roads, ports/airports, cars, yatchs, planes and houses... of the very few making money by the press of a button (no wonder why they have so much free-time to enjoy life).
The only way for them to keep being your masters was the same used to become your masters: they exclude you from all the jobs, contracts and funding so that you will never be able to compete with them – and your kids, excluded from the best schools and universities, will have to perpetuate this planned injustice... enforced by our governments (the ones paid by the taxpayer to serve his needs)!
This has reach such levels that even the most reputed universities (like Harvard here) indicate that "a majority of white Americans say discrimination against whites exists in America today".
This constant discrimination explains the GAFAM dominance based on infinite magic-money created by public-debt, out of thin air: commercial banks are private but their electronically-created money (~97% of the monetary mass, ~3% being the now-public 'banknotes' and coins) is guaranteed by public governments, that is, you and me... and all our tangible assets (land, buildings, production tools) have been engaged by governments on our behalf as the sole guaranty of all these virtual deposits (bank accounts).
Bankers inflate public-expenses and therefore public-debt to make the financial system crumble-down, so that they can pay themselves by activating the government guaranty – transferring all our tangible assets in their pockets.
This is why, between 1924 and 2023, according to the U.S. Treasury, the total U.S. monetary mass grew exponentially by 1,560 (33,167,334,044,723 / 21,250,812,989 September 2023 being the latest available number at the time we wrote this).
In the past, banks going belly-up (because of outright fraud, bad investments and/or hazardous speculation) were destroying the investment of their shareholders.
Today, the "rule of law" has been modified to let banks compensate their deficits with the deposits of their clients – including the tangible assets of the population managed by their public-debtors if their own currently available balance of fiat money revenue and deposits are not covering their public-debt.
A debt that was conveniently made impossible to pay back with normal interest-rates – after a long period of anemic interest-rates boosting public-debt like never before in the History of Capitalism.
The consequences of enjoying the money-creation monopoly (stolen from all Nations by the private bankers) is easy to understand. To increase their powers, they must create much more money than possible in normal times, so bankers:
- hate efficiency and peace, and they love waste, wars, natural destructive events, and pandemics,
- will do everything their can to artificially create trouble, food/water/energy scarcity and political/financial crises,
- will eventually own the World... thanks to the assistance of the governments supposedly defending the public interest.
As a result, anyone avoiding or reducing the impact of these existential threats will be seen by the bankers as an enemy. There's no wonder about why we have such a sorry state of things, with increasingly cumulated catastrophes:
"For at least another hundred years we must pretend to ourselves and to every one that fair is foul and foul is fair; for foul is useful and fair is not. Avarice and usury and precaution must be our gods for a little longer still. For only they can lead us out of the tunnel of economic necessity into daylight."
– John Maynard Keynes, English economist (1883-1946), "Essays in Persuasion" (1931)
Keynes wrote this just before WWII, which was created to eliminate Germany as an economic threat to the "international bankers" because:
"Germany issued debt-free and interest-free money from 1935 and on, accounting for its startling rise from the depression to a world power in 5 years. Germany finance[d] its entire government and war operation from 1935 to 1945 without gold and without debt, and it took the whole Capitalist and Communist world to destroy the German power over Europe and bring Europe back under the heel of the bankers. Such history of money does not even appear in the textbooks of public (govemment) schools today."
– Pastor Sheldon Emry, "Billions for the Bankers, and Debts for the People"
After its destruction in WWI, Germany just replicated what the US had done before becoming owned by the "international bankers" that then created WWII to destroy Germany again:
"History tells us of debt-free and interest-free money issued by governments. The American colonies did it in the 1700's and their wealth soon rivaled England and brought restrictions from Parliament, which led to the Revolutionary War. Abraham Lincoln did it in 1863 to help finance the Civil War. He was later assassinated by an agent of the Rothschild Bank. No debt-free or interest-free money has been issued in America since then."
– Pastor Sheldon Emry, "Billions for the Bankers, and Debts for the People"
Make no mistake: the only sustainable way for robbers to keep their stolen bounty is to kill the previous owners (so that their can't try to get it back) – and to destroy the possibility for their slaves to ever consider destituting them. This requires the robbers to take all the powers, over all the Planet, and to reduce to ever-lasting impotence the very few slaves allowed to survive.
If History is of any guidance to understand what's next, with ever-greater abuses as time goes, such a toxic mix of incompetence and duplicity will not end well.
The only way out is to exit their traps (a treacherous economy bringing the oposite of the promissed "Justice", "Freedom" and "Wealth") and to undo the damage they inflicted us (because we all were born to be free rather than to be trapped and enslaved):
- stop trying to please our masters, they just want you to make horrible choices – like betraying everyone – or to fertilize,
- stop opposing your neighbors' views on politics and religion, the pursued goal is to split our forces to divide us – because we are the many and they are the very few,
- start doing business with those in need to build strong balanced relations, to participate to the changes you want to see happening, and to build the World we all want to transmit to our kids.